What Does Open Port Mean?
Before going deeper into checking open ports, let's first know what open ports mean. An Open Port or a listening port is the port in which some application is running. The running application listens on some port, and we can communicate with that application over that listening port. If an application is running on a port, and we try to run another application on the same port, the kernel will throw an error. That is one of many reasons we check for open ports before running applications.
List Open Ports Using nmap
Network Mapper, known as nmap, is an open source and free tool, which is used to scan ports on a system. It is used to find vulnerabilities, discover networks, and find open ports. In this section, we will use nmap to get a list of open ports on a system. First of all, update cache on Ubuntu before installing nmap:
[email protected]:~$ sudo apt-get update -yNmap can be installed using the following command in the terminal:
[email protected]:~$ sudo apt-get install nmap -yAfter installing nmap, verify the installation by checking the version of the nmap:
[email protected]:~$ nmap --version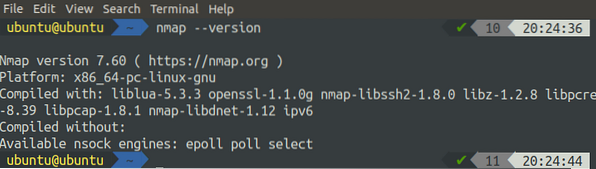
If it gives the version of nmap, then it is installed perfectly, otherwise, try the above commands again to install nmap properly. Nmap is used to perform several related to networks, and port scanning is one of those tasks. The nmap tool is used along with many options. We can get the list of all the available options by using the following command:
[email protected]:~$ man nmapSo, to scan your localhost, use the apprehended command below:
[email protected]:~$ sudo nmap localhost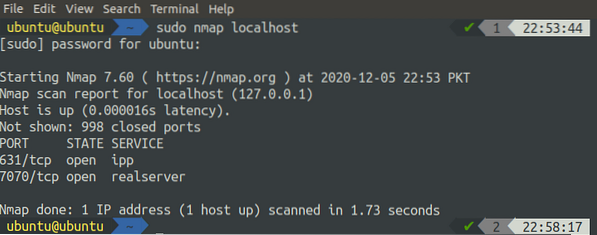
It will list all the open ports on localhost, as displayed in the above image. We can also use nmap to scan remote hosts:
[email protected]:~$ sudo nmap 93.184.216.34Also, we can use the hostname of the remote server instead of an IP address:
[email protected]:~$ sudo nmap www.example.comThe nmap command can also be used to scan a range of IP addresses. Specify the range of IP Addresses in the command, as in the command below:
[email protected]:~$ sudo nmap 192.168.1.1-10The above command will scan all the IP addresses from 192.168.1.1 to 192.168.1.10, and it will display the result in the terminal. To scan ports on a subnet, we can use nmap as follows:
[email protected]:~$ sudo nmap 192.168.1.1/24The above command will scan all the hosts with IP addresses in the subnet defined in the command.
Sometimes you have to scan ports on random hosts, which are in different subnets and are not in sequence, then the best solution is to write a hosts file in which all the hostnames are written, separated by one or more spaces, tabs, or new lines. This file can be used with nmap as follows:
[email protected]:~$ sudo nmap -iL hosts.txt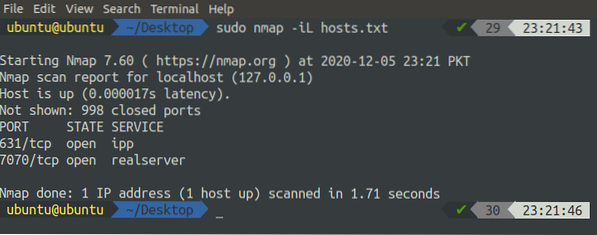
We can use nmap to scan a single port on the system by specifying the port using the '-p' flag, along with nmap, as in the following command:
[email protected]:~$ sudo nmap -p 80 localhost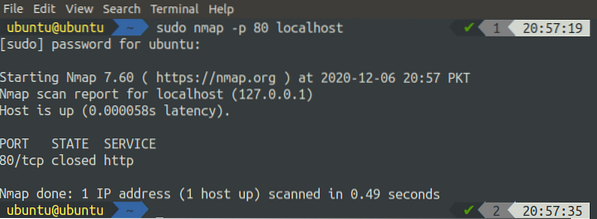
Range of ports can also be scanned on a system using nmap in the following way:
[email protected]:~$ sudo nmap -p 80-85 localhost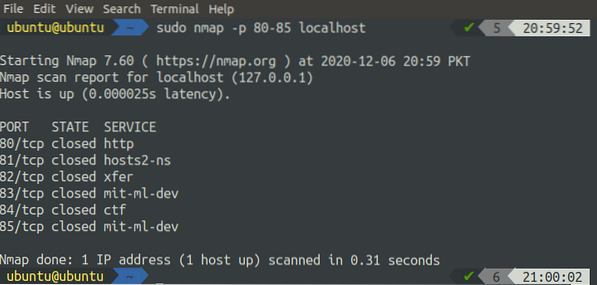
We can scan all the ports of a system using nmap:
[email protected]:~$ sudo nmap -p- localhost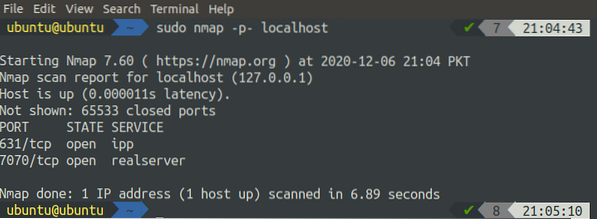
To get a list of the most commonly open ports on your system, you can use the nmap command with the '-F' flag:
[email protected]:~$ sudo nmap -F localhost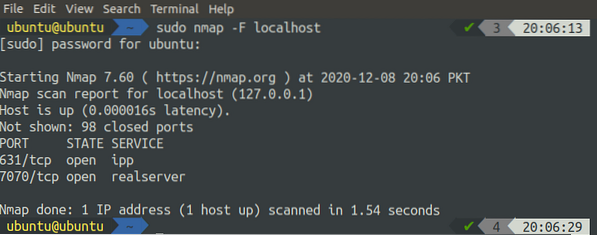
TCP ports can be scanned on the system using nmap by just adding the '-T' flag, along with the nmap command:
[email protected]:~$ sudo nmap -sT localhost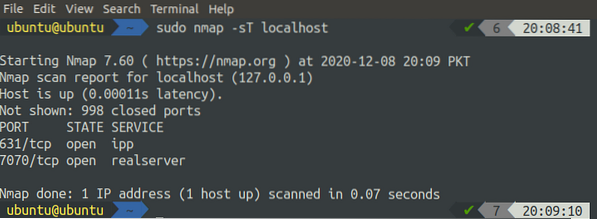
Similarly, for UDP ports, you can use the '-U' flag with the nmap command:
[email protected]:~$ sudo nmap -sU localhost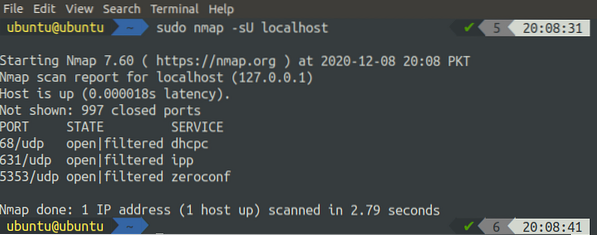
List Open Ports Using lsof
The lsof command, also known as 'list open files', is used to get the information about open files used by different processes in UNIX and LINUX like operating systems. For most of the Linux distros, this tool comes pre-installed. We can verify the installation of lsof by just checking its version:
[email protected]:~$ lsof -v
If it does not show the version, then lsof is not installed by default. We can still install it using the following commands in the terminal:
[email protected]:~$ sudo apt-get update -y[email protected]:~$ sudo apt-get install lsof
We can use the lsof command along with different options. The list of all the available options can be displayed using the following command in the terminal:
[email protected]:~$ man lsofNow, in this section, we are going to use lsof to display ports of a system in different ways:
[email protected]:~$ sudo lsof -i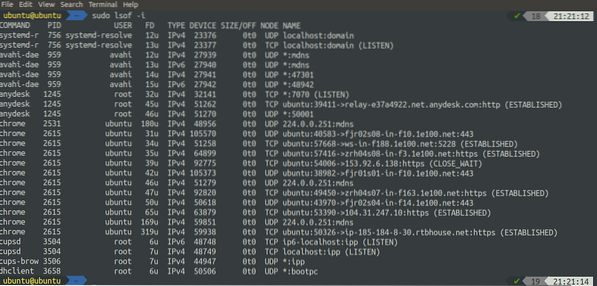
The above command has displayed all the open ports. We can also use the lsof command to display all the open sockets:
[email protected]:~$ sudo lsof -n -P | grep LISTEN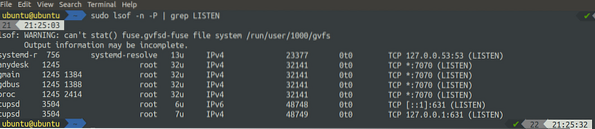
We can list filtered ports based on a protocol using lsof. Run the command given below to list all the TCP Connection types:
[email protected]:~$ sudo lsof -i tcp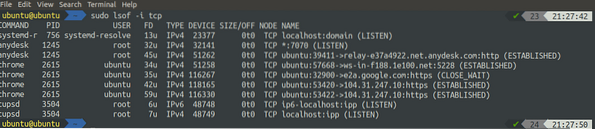
Similarly, we can list all the UDP connection types using lsof in the following way:
[email protected]:~$ sudo lsof -i udp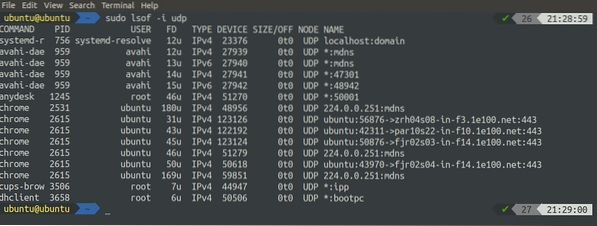
List Open Ports Using netstat
The netstat, also known as network statistics, is a command line program used to display detailed information about networks. It displays both incoming and outgoing TCP connections, routing tables, network interfaces, etc. In this section, we will use netstat to list open ports on a system. The netstat tool can be installed by running the following commands:
[email protected]:~$ sudo apt-get update -y[email protected]:~$ sudo apt-get install net-tools -y
After running the above commands, you can verify the installation by checking the netstat version:
[email protected]:~$ netstat --version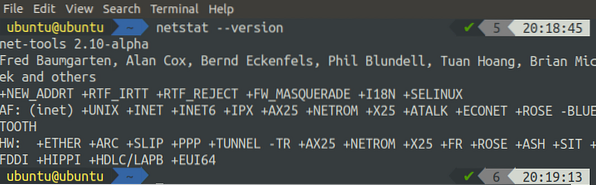
If it displays the version of net-tools, then the installation is fine, otherwise, run the installation commands again. To get an overview of all the available options that can be used, along with the netstat command, run the following command:
[email protected]:~$ man netstatWe can get a list of all the listening ports using the netstat command in Ubuntu by running the following command:
[email protected]:~$ sudo netstat -l
The netstat command can also be used to filter listening to the TCP and UDP ports by just adding a flag along with the command. For listening to the TCP ports:
[email protected]:~$ sudo netstat -lt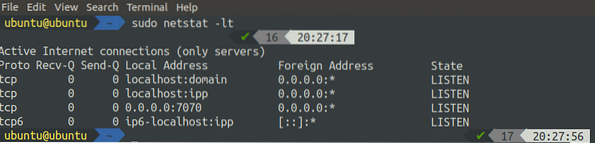
For listening to the UDP ports, use the following command:
[email protected]:~$ sudo netstat -lu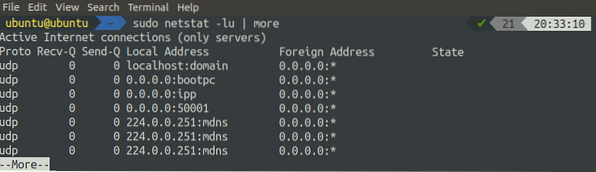
To get the list of all the listening UNIX ports, you can run the following command in the terminal:
[email protected]:~$ sudo netstat -lx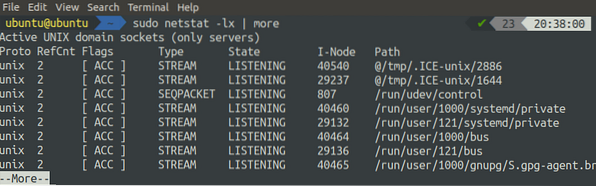
List Open Ports Using ss
The ss command is used to display information about sockets in a Linux system. It displays more detailed information about sockets than the netstat command. The ss command comes pre-installed for most of the Linux distros, so you do not need to install it before using it. You can get a list of all the options, which can be used along with the ss command, by running the 'man' command with ss:
[email protected]:~$ man ssTo get a list of all the connection regardless of their state, use the ss command without any flag:
[email protected]:~$ sudo ss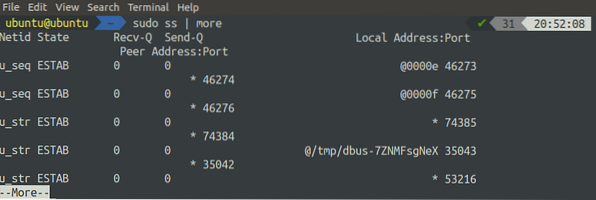
To get a list of all the listening ports, use the ss command with the '-l' flag. The '-l' flag is used to display only listening ports:
[email protected]:~$ sudo ss -l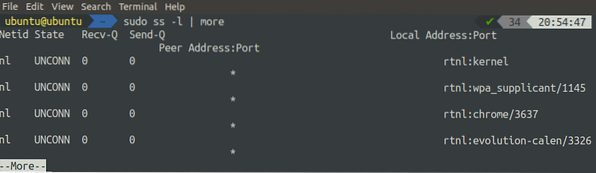
To get all the listening TCP ports, we can use the '-t' and '-l' flag along with the ss command:
[email protected]:~$ sudo ss -lt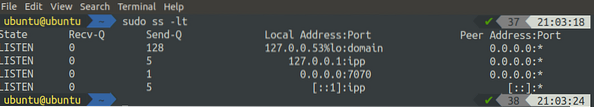
Similarly, we can get a list of all the listening UDP ports using the ss command along with the '-u' and '-l' flag:
[email protected]:~$ sudo ss -lu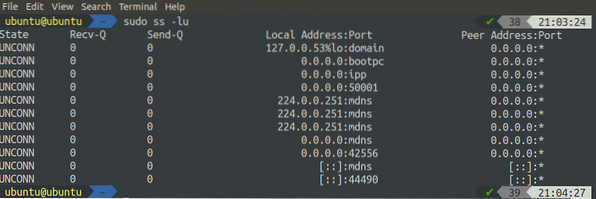
The ss command can also be used to get a list of all the connections with the source or the destination port. In the following example, we are going to get the list of all the connections with the destination or source port 22:
[email protected]:~$ sudo ss -at '( dport = :22 or sport = :22 )'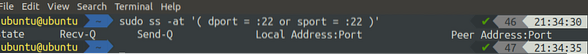
You will get a list of all the inbound and outgoing connections if you have connected to a remote system using ssh.
Conclusion
For system administrators, security professionals, and other IT related persons, it is important to be aware of the open ports on the servers. Linux is rich with the tools used to diagnose networks and provides many tools that can be helpful for various kinds of networking activities. In this tutorial, we have used some tools like netstat, ss, lsof, and nmap to check for open ports on Ubuntu. After going through this article, you will be able to easily list all the listening ports on your Linux server in many ways.
 Phenquestions
Phenquestions


